간디의 세상
[CyberGon CTF 2024] WriteUp 본문

Solved some Osint' and a Stegano, Crypto, Reconnaissance
OSINT
Favorite Journal
The Statue
Vacation(1)
STEGANO
Truesight
Crypto
RSA1
Reconnaissance
Secure Life
OSINT
Favorite Journal

A page of the journal is provided
https://www.learnbig.net/th/books/shwe-thway-vol-45-no-15/
ชเวธาเวย์ Vol. 45 ฉบับที่ 15 Thingyan ล้มลง ลุกขึ้น ลุกขึ้
ชเวธาเวย์ Vol. 45 ฉบับที่ 15 Thingyan ล้มลง ลุกขึ้น ลุกขึ้นชเวธาเวย์ Vol. 45 ฉบับที่ 15 Thingyan ล้มลง ลุกขึ้น ลุกขึ้
www.learnbig.net
Using Google Lenz and translation, we can find it was a page of 'Shwe Thway Vol. 45 and No.15'
We have to find its published date and print house registrantion number of Vol.1 and No.1
https://sites.google.com/view/haytha-yu-mon/shwe-thway-vol-01-1969
Haytha Yu Mon - Shwe Thway Vol. 01, 1969
ရွှေသွေးဂျာနယ် အတွဲ ၁ အမှတ် ၁ မှ ၂၆ ၊ ၁၉၆၉ ခုနှစ် Shwe Thway Vol. 01, 01-26, 1969 https://drive.google.com/open?id=1it9tz0nUMDGDb6onYsF1D5KO2pAjF3lB https://www.mediafire.com/f
sites.google.com
From here we can find Vol.1 and No.1 pdf scan file

The cover of Vol.1 and No.1
On left-bottom side, the published date is written
But google translation does not working well..
So I searched Myanmar language and translated myself
It says published April 1st in 1969

Last page has information of printing house
Using Google image text translation, it was printed at the Temple of Literature Printing House
Registration Number is 0032
So we can make flag
CYBERGON_CTF2024{4-1-69_0032}
I'm not familiar with foreign languages, so it took a long time..
The Statue

The image of statue was given
We can find where it is easily by using Google Lenz

In Google Map its name is 'Maha Bodhi Ta Htaung Standing Buddha'


Large square tiles in front of stairs are approximately three
So if you pin four blocks ahead of stairs given camera angle, you can get 22.0801, 95.2885 coordinations
CYBERGON_CTF2024{22.0801_95.2885}
Vacation (1)

A png file was given but cannot open it
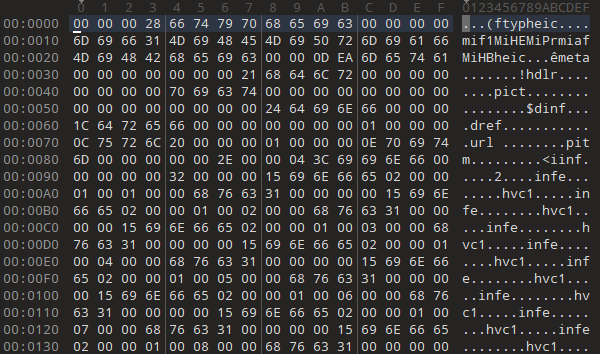
Opening it with 010Editor, the following four letters after 'ftyp' means what type of this image
So this file is HEIC file, the general HEIF image
If you take a photo with Galaxy Phone or something, that photo file type is HEIF file
But we can't open it with Window default photo viewer

Using Online Converter, you can convert HEIF to PNG
By using Google Lenz, you can guess here is Ha Long in Vietnam easily

We can get some hints through the direction of the Ferris wheel and the roller coaster rails
Find a place with a roller coaster facing the Ferris wheel

There are two buildings but i think the photo was taken at left building of above screenshot
But they are same hotel so hotel's name is 'Muong Thanh Luxury Ha Long Centre Hotel'
CYBERGON_CTF2024{Muong Thanh Luxury Ha Long Centre Hotel, Ha Long, Vietnam}
STEGANO
Truesight

PNG file cannot be opened

We can guess it is png file format through IHDR and RGB etc.
But without File Signature
PNG file's Signature Hex is '89 50 4E 47 0D 0A 1A 0A'


After adding file signature you can get correct image file withour error
And the flag is fully displayed in image
CYBERGON_CTF2024{y0u_g07_7h3_r!gh7_s1gn5}
CYRPTO
RSA1
# crypto.py
from Crypto.Util.number import getPrime, bytes_to_long
from math import gcd
flag = "XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX"
FLAG = flag.encode()
out = open('output.txt', 'w')
rsa_q = getPrime(512)
rsa_p = getPrime(512)
n = rsa_q * rsa_p
exp1 = 0x10003 #65539
exp2 = 0x10001 #65537
assert gcd(exp1, exp2) == 1
assert gcd(exp1, n) == 1
assert gcd(exp2, n) == 1
def encryption(plaintext):
cip1 = pow(plaintext, exp1, n)
cip2 = pow(plaintext, exp2, n)
return (cip1, cip2)
cip1, cip2 = encryption(bytes_to_long(FLAG))
out.write("n = "+ str(n)+ "\ncip1 = "+ str(cip1)+ "\ncip2 = "+str(cip2))
out.close()Encoding code and output txt file including n, cip1 and cip2 are given
Simple RSA challenge
gcd function is for getting greatest common divisor
from Crypto.Util.number import inverse, long_to_bytes
n = 157508528276758767638734754424621334466394815259243977959210580239577661657714722726225362774231543920376913579658052494826650164280151836289734452590647102313381584133512835595817708427222746495824286741840967127393187086028742577763080469063534742728547285121808241078515099307495843605080694383425986909029
cip1 = 69950256754119187070741220414057295159525964023691737870808579797990094306696842507546591858691032981385348052406246203530192324935867616305070637936848926878022662082401090988631324024964630729510728043900454511012552105883413265919300434674823577232105833994040714469215427142851489025266027204415434792116
cip2 = 26975575766224799967239054937673125413993489249748738598424368718984020839138611191333159231531582854571888911372230794559127658721738810364069579050102089465873134218196672846627352697187584137181503188003597560229078494880917705349140663228281705408967589237626894208542139123054938434957445017636202240137
e1 = 65539
e2 = 65537
def extended_gcd(a, b):
if b == 0:
return a, 1, 0
g, x1, y1 = extended_gcd(b, a % b)
x = y1
y = x1 - (a // b) * y1
return g, x, y
_, x, y = extended_gcd(e1, e2)
m1 = pow(cip1, x, n)
m2 = pow(cip2, y, n)
m = (m1 * m2) % n
flag = long_to_bytes(m)
print("FLAG:", flag.decode())Using extended euclidean algorithm, you can decode flag
Actually I didn't understand this algorithm at all.. so I just use it mechanically;;
CYBERGON_CTF2024{54m3_m0Du1u5!!!!!}
Chill Bro
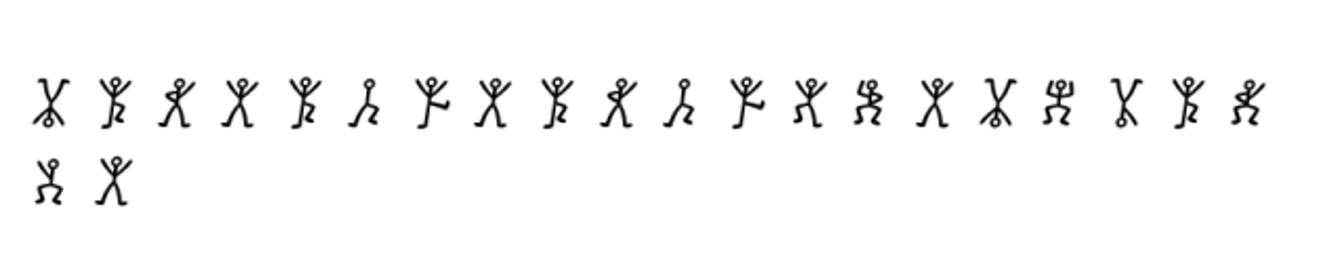
Given some human postures image
At first, I tried to match some alphabet to each postures but cannot progress anymore
This CTF was so hard for me (I am beginner), so I read some writeups in 2023 CyberGon CTF
And then I found there are soooo many kind of symbols ciphers in dCode site

I found it is dancing men cipher
Decoding it, get flag
CYBERGON_CTF2024{TAKEABREAKBROLETSDANCE}
Reconnaissance
Secure Life
certificate.der file was given
I'm not familiar with this file format but as i searched, it used as certification key or data

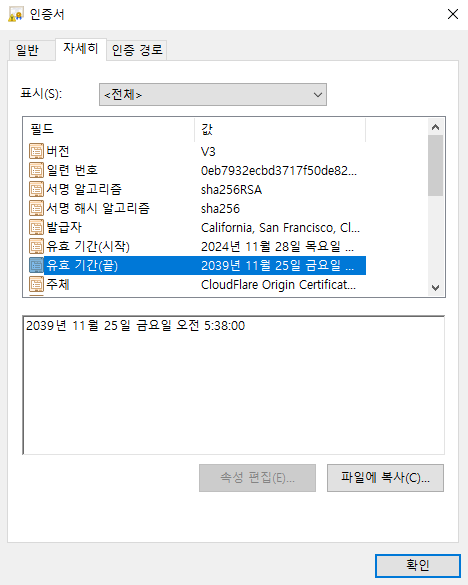
You can just open this file in Windows, and view expiration date and time
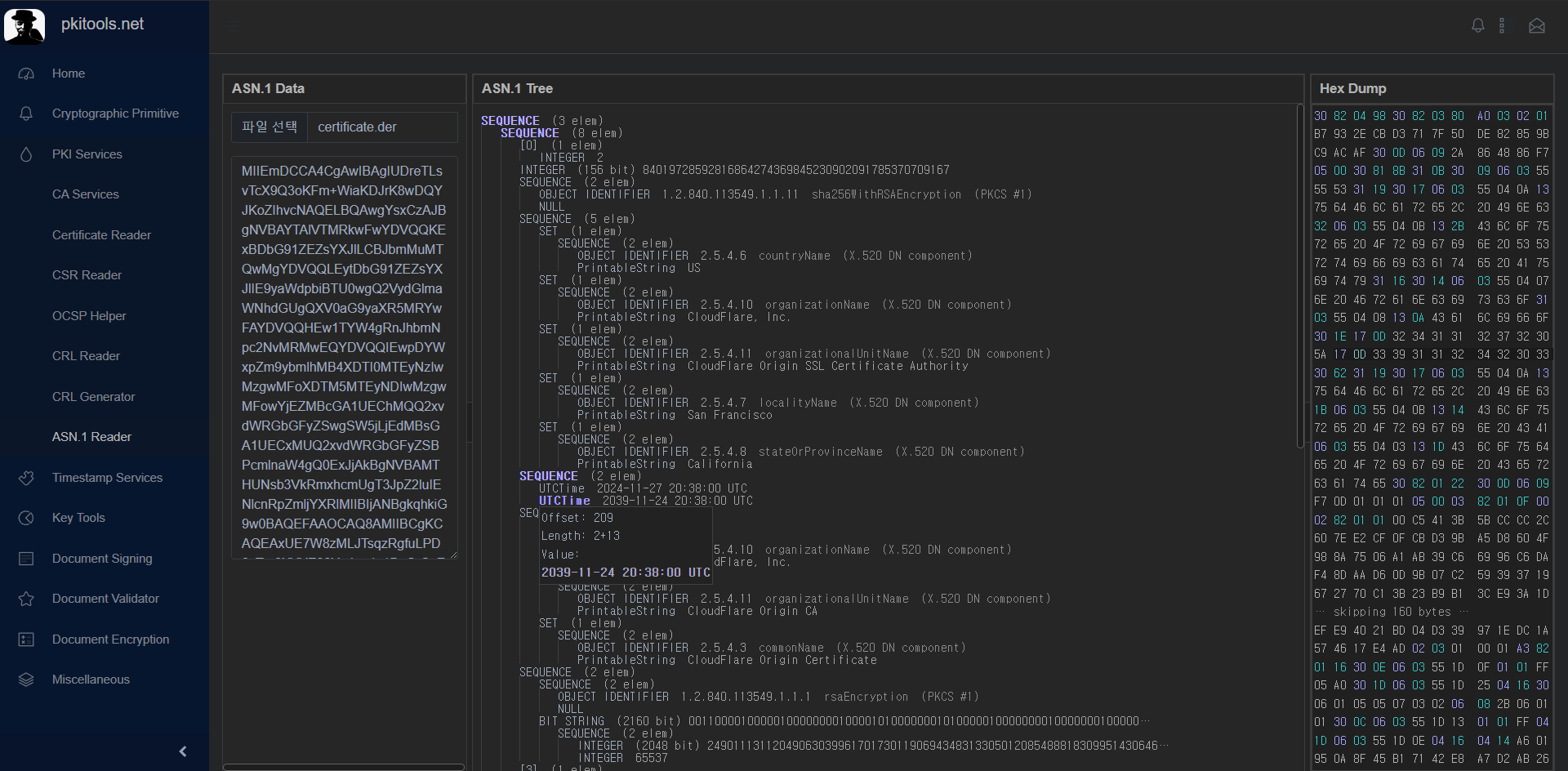
But when I solve this challenge, I didn't think to open the file in windows directly
I thought it will not open well
So I used pkitools.net to parse this file
And found date estimated as expiration
CYBERGON_CTF2024{2039:11:24:20:38:00}
엄청 오랜만에 CTF 풀어봤다
반수하다 오니까 감이 다 뒤진 것 같다;;
괜히 했나.. 1년간 변화가 없다
웹이고 포렌식이고 분야도 다양하고 문제도 되게 많아서 많이 시도해봤는데 될 것 같으면서도 안 되는게 많았다
결국 하나도 못 풀었는데 끝나고 디코에서 사람들 하는 얘기 들어보니까 너무 허무하게 풀리는 것들이었다
대부분 플래그 얻기 바로 전 단계에서 막혀서 좀 아쉬웠다
아무튼 영어 공부도 좀 할 겸 영어로 써봤는데 제대로 쓴 건지 모르겠다
문제도 어렵지 않은 것만 풀었고 사진만 봐도 이해가 갈 터이니 그냥 별 신경 쓰지 않기로 한다
'Security > CTF' 카테고리의 다른 글
| [LA CTF 2025] Write Up (0) | 2025.02.10 |
|---|---|
| [SSU CTF 2025] Writeup (0) | 2025.01.25 |
| SecurityFACT CTF w. Alkon 2024 Writeup (0) | 2024.11.16 |
| 2024 5월 Space War Web WriteUp (0) | 2024.05.12 |
| [AmateurCTF 2024 Write Up] 동아리 팀으로 나간 CTF (0) | 2024.04.14 |
| [LA CTF 2024 Write UP] 두번째로 참가해본 CTF (0) | 2024.02.19 |




